Introduction:
In the modern-day age of digital advancements, the protection of personal data from cyber threats has assumed paramount importance. Cyber Security software assumes a crucial position in the realm of defense by providing an extensive array of tools and technologies specifically engineered to safeguard against, identify, and address security risks. It is imperative for both enterprises and individuals to possess a comprehensive comprehension of these technologies and effectively utilize them.
In this article, we will delve into the mainstream Cyber Security Software used by premier security experts
What is Cyber Security Software?
The term “cybersecurity software” encompasses a range of technologies that are specifically developed to safeguard digital devices, networks, and systems against unauthorized access, malicious attacks, or potential harm. These technologies are designed to actively monitor, detect, report, and mitigate cyber threats, thereby safeguarding the integrity and confidentiality of data.
Types of Cyber Security Software
There exists a wide range of cybersecurity software, each specifically tailored to address distinct threats and vulnerabilities, such as mentioned in the following table:
| Antivirus and Anti-malware Solutions | Implement robust security measures to safeguard computer systems from the infiltration and detrimental effects of viruses, worms, trojans, and other forms of harmful software. |
| Firewalls | The task involves monitoring the flow of network data, both incoming and outgoing, and making determinations on the permission or restriction of specific traffic based on pre-established security protocols. |
| Intrusion Detection and Prevention Systems (IDPS) | The task at hand involves the monitoring of network traffic with the objective of identifying any instances of malicious activity or violations of established policies. |
| Encryption Tools | The encryption of data serves as a protective measure against illegal access. |
| Security Information and Event Management (SIEM) Systems | Provide instantaneous analysis of security alarms produced by various hardware and software systems. |
What is the Use of Cyber Security Tools and Software?
These technologies serve to secure digital assets against cyber threats, so ensuring the uninterrupted operation of businesses, safeguarding sensitive data, and aiding in the fulfillment of regulatory compliance requirements. In addition, cyber security software and technologies play a crucial role in safeguarding digital assets, systems, and networks from malicious assaults, illegal access, and potential breaches.
They provide a crucial function in the protection of sensitive data, guaranteeing the uninterrupted operation of businesses, and upholding the reliability and accessibility of information. These technologies have the capability to constantly monitor digital surroundings for any irregularities, hence aiding in the timely detection of possible dangers.
Additionally, they offer ways to swiftly address and mitigate these threats. Furthermore, they provide support to firms in attaining and sustaining regulatory compliance through consistent adherence to data protection standards. In addition, cyber security software and technologies tend to be the primary barrier in the digital domain, safeguarding operations and transactions within an ever more linked global landscape.
How do Cyber Security Tools and Software Work?
The distinguished cyber security software and tools work to complete the several tasks assigned to them by the security professionals. Moreover, their working methodology can be further divided into the following steps:
| Monitoring | It is imperative to maintain continuous surveillance of systems in order to detect any abnormal behaviors. |
| Detection | This inquiry seeks to identify common patterns that are typically observed in cyber-attacks. |
| Alerting | Inform the system administrators of possible security breaches. |
| Response | Take action against recognized threats, such as the removal of dangerous software or the blocking of IP addresses. |
| Updates | It is imperative to consistently upgrade systems in order to safeguard against the most recent known threats and vulnerabilities. |
Benefits of Cyber Security Software
Multiple benefits of cyber security software have been recorded periodically by several people and organizations. Some of the prominent benefits of cyber security software include the following:
| Proactive Defense | Cybersecurity software offers proactive defense mechanisms by continuously monitoring, identifying, and mitigating potential threats in real-time, preventing any potential harm, as opposed to adopting a reactive approach after an incident has occurred. |
| Data Protection | These solutions provide protection for sensitive and crucial data, preventing illegal access and protecting the confidentiality of personal, financial, and corporate information. |
| Business Continuity | Cybersecurity software plays a crucial role in safeguarding against and mitigating cyberattacks, hence minimizing disruptions to business operations. This proactive approach ensures the continuity of business activities and mitigates potential financial losses. |
| Boosted Customer Trust | The implementation of robust cybersecurity measures and the utilization of sophisticated tools by firms can significantly bolster confidence among clients and customers, particularly for enterprises that handle sensitive customer data. |
| Compliance and Regulation | Numerous industries are subject to distinct cybersecurity legislation. The utilization of cybersecurity software enables firms to comply with regulatory standards, thereby mitigating the risk of incurring financial penalties and legal consequences. |
| Prevention of Financial Losses | Cyberattacks have the potential to cause substantial financial harm as a consequence of business disruptions, loss of data, or the imposition of ransom demands. Cybersecurity tools serve to mitigate the aforementioned threats. |
| Protects Brand Reputation | The reputation of a corporation might be negatively impacted by a solitary instance of a security breach. By implementing strong cybersecurity protocols, organizations may effectively uphold and enhance their brand reputation. |
| Advanced Threat Intelligence | Numerous contemporary cybersecurity solutions offer businesses the advantage of insights and analytics obtained from a comprehensive global threat intelligence network. These solutions enable organizations to anticipate and proactively address emerging risks. |
| Scalability and Flexibility | As enterprises expand, the challenges they encounter tend to become increasingly intricate. Cybersecurity software possesses the capability to be scaled and modified in order to effectively address the ever-changing requirements. |
| Employee Protection | In addition to safeguarding company data, these tools also provide protection for employees’ personal information and establish a secure digital working environment. |
List of Cyber Security Software Tools
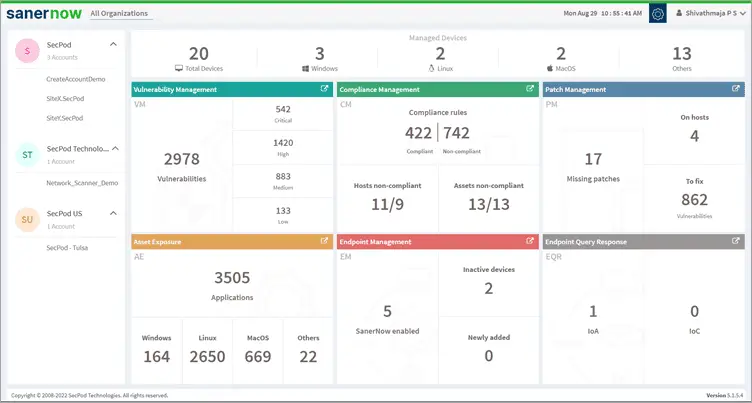
#1) SecPod SanerNow
Best for small to large organizations.
The Saner Now cyber hygiene platform offers a sophisticated vulnerability management solution that enables the ongoing assessment of security risks and compliance status, hence aiding in the avoidance of cyber-attacks. The platform is a sophisticated vulnerability management system that combines vulnerability evaluation and immediate repair inside a unified UI.
The software scans to identify vulnerabilities, misconfigurations, and other potential issues. It also offers remediation controls and techniques to promptly and automatically address these identified issues.
The vulnerability management process can be fully automated through the utilization of a system that is designed in-house, enabling the automation of each stage, including scanning and remediation. SanerNow assists in enhancing an organization’s security stance and mitigating the risk of cyberattacks.
Features:
- The system employs an intelligent and efficient multi-functional agent that carries out various activities.
- SanerNow effectively prioritizes vulnerabilities for convenient treatment by conducting risk potential assessments and considering high-fidelity attacks, among other factors.
- With its integrated patching, you can quickly fix vulnerabilities in IT assets.
- By implementing remediation rules that go beyond simple patching, the process of reducing security threats is facilitated.
- Through the utilization of a unified cloud-based console, your firm may effectively address vulnerabilities and other related concerns in an expedient manner.
- SanerNow enables users to engage in real-time vulnerability management, encompassing the entire process from scanning for vulnerabilities to implementing repair measures.
Category: A tool for managing vulnerabilities and patches in both cloud and on-premises environments.
Verdict:
SanerNow offers a comprehensive cybersecurity solution that enhances the vulnerability management process by enabling the management of additional security threats through a unified console. Moreover, it has the potential to substitute other systems employed for vulnerability management and patch management, hence enhancing the efficiency of managing attack surfaces.
Cost: Contact SecPod SanerNow for a quote.
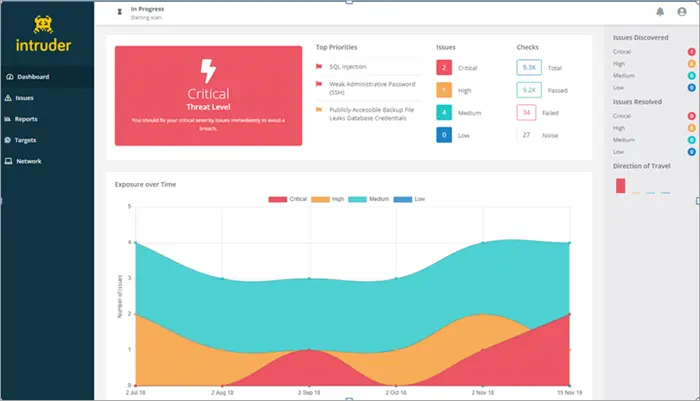
#2) Intruder
Best for small to large businesses.
Cost: A complimentary trial period of 14 days is offered. The pricing structure comprises three distinct plans, namely Essential, Pro, and Verified. Please reach out to them for any clarification regarding their price specifics.
Intruder is a widely utilized cloud-based network vulnerability scanner that aids in the identification of cybersecurity vulnerabilities within highly susceptible systems, hence mitigating the risk of costly data breaches. This solution is deemed appropriate for addressing your cybersecurity concerns. It significantly aids in the conservation of time.
Features:
- There are more than 9,000 security flaws.
- The service offers an unrestricted number of scans upon request.
- The system allows for an unlimited number of user accounts to be created.
- This study examines the identification and detection of vulnerabilities in web applications, specifically focusing on two common flaws: SQL injection and Cross-site scripting.
- Notifications regarding emerging threats.
- Smart Reconnaissance
- Network view
- PCI ASV scans are available.
Category: Cloud-based Vulnerability Scanner
Verdict: Intruder serves as a comprehensive solution catering to various cybersecurity requirements.
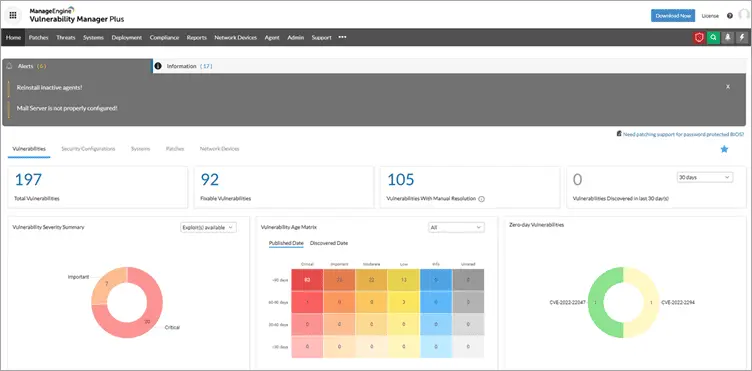
#3) ManageEngine Vulnerability Manager Plus
ManageEngine Vulnerability Manager Plus is a software solution designed for organizations that emphasize prioritizing threat and vulnerability management. It includes a built-in patch management feature.
The proposed approach offers a strategic resolution for providing a broad range of capabilities, including visibility, assessment, remediation, and reporting of vulnerabilities, misconfigurations, and other security weaknesses throughout the company network. These functionalities are managed from a centralized interface, enhancing the efficiency and effectiveness of the overall security framework.
Features:
- Conduct a risk-based vulnerability assessment to evaluate and prioritize vulnerabilities that are exploitable and have a significant impact.
- The process of automating and customizing patches for operating systems such as Windows, macOS, and Linux.
- The task involves the identification of zero-day vulnerabilities and the implementation of interim solutions prior to the arrival of permanent fixes.
- The practice of consistently identifying and resolving misconfigurations through the implementation of security configuration management.
- Obtain security guidelines for configuring web servers in a manner that is devoid of many attack versions.
- Conduct an examination of end-of-life software, peer-to-peer and unsecured remote desktop sharing software, as well as active ports inside your network.
Category: Comprehensive solution for managing threats and vulnerabilities within an organization’s on-premises infrastructure.
Verdict: ManageEngine Vulnerability Manager Plus is a comprehensive software solution designed to address vulnerabilities across several operating systems. In addition to its primary function of detecting vulnerabilities, this software also incorporates a built-in remediation feature to effectively mitigate identified vulnerabilities.
Vulnerability Manager Plus provides a diverse range of security functionalities, including security configuration management, automated patching, web server hardening, and high-risk software auditing. These capabilities aim to establish a secure framework for your endpoints.
#4) ManageEngine Log360
Best for Internal and External threat protection.
Cost: Contact for a quote. A 30-day free trial is available with the parent organization.
Log360 provides a cybersecurity system that uses machine learning algorithms to identify and mitigate security risks. The platform is equipped with an integrated threat intelligence database, enabling the tool to effectively address both historical and emerging risks. The application can also be utilized for the purpose of effectively managing security incidents in real-time, by leveraging configurable notifications.
Features:
- Threat Intelligence
- Behavior Analytics
- Data Visualization
- Compliance Reporting
- Incident Management
Verdict: Log360, developed by ManageEngine, is widely regarded as a top-tier Security Information and Event Management (SIEM) solution due to its exceptional capabilities in identifying network threats, assessing potentially malicious user actions, and mitigating the risk of data loss.
#5) SolarWinds Security Event Manager
Best for small to large businesses.
Cost: The software offers a comprehensive trial period of 14 days, during which all features and functionalities are freely accessible. The price of the product commences at $4500.
The SolarWinds Security Event Manager is an intrusion detection solution designed for both network and host environments. The system conducts continuous monitoring, prompt response, and comprehensive reporting of security threats in real-time. The system possesses advanced log search capabilities with great indexing efficiency. The system is built on cloud technology and is capable of scaling to meet varying demands.
Features:
- The field of threat intelligence undergoes ongoing updates.
- It possesses functionalities pertaining to Security Information and Event Manager.
- The software provides functionalities related to log correlation and log event archiving.
- It also offers a comprehensive suite of integrated reporting tools.
Category: Cloud-based tool for SIEM.
Verdict: SolarWinds Security Event Manager (SEM) is a cloud-based software solution designed specifically for Managed Service Providers (MSPs). It serves as a comprehensive and integrated Security Information and Event Management (SIEM) tool.
#6) Norton Security
Cost: Norton offers a complimentary 30-day trial period for its Antivirus software. The cost of antivirus software begins at a monthly rate of $5.99. The initial cost of Norton 360 with LifeLock is $9.99 for a period of three months.
Norton offers a comprehensive solution by means of Norton 360 with LifeLock, encompassing several features and functionalities. The company provides a range of cybersecurity software solutions, including Antivirus, Virus Removal, Malware Protection, Cloud Backup, Password Manager, and Secure VPN.
Features:
- Norton Antivirus is capable of providing protection against a range of online dangers, including but not limited to ransomware, viruses, spyware, malware, and various other forms of malicious software.
- The system offers a comprehensive five-tier defense mechanism for the identification and mitigation of potential security risks.
- The company provides cloud-based backup services that facilitate the storage and safeguarding of various files and documents.
- The Norton Password Manager is an efficient and reliable tool for effectively storing passwords, ensuring their security, and employing intelligent features.
- The Norton VPN offers a reliable and secure virtual private network service.
Verdict: The Norton security solution encompasses a range of protective measures designed to safeguard PCs, smartphones, and tablets. There are several options available, including antivirus software, password managers, and virtual private networks (VPNs).
#7) McAfee
Best for Multi-faceted security protection.
McAfee provides comprehensive security measures to users through a combination of top-tier privacy, identity protection, and antivirus products. Once the software is implemented, it will provide real-time protection against a variety of cyber threats, including ransomware, viruses, phishing schemes, adware, malware, and other malicious activities. One notable advantage of McAfee is its ability to safeguard up to 10 distinct devices with a single subscription.
Features:
- Antivirus protection
- Complete Firewall protection
- Full Internet Protection
- Password Manager
- Encrypted Storage
Verdict: McAfee is an effective cross-platform cybersecurity solution that offers comprehensive protection against a wide range of threats in real-time across many devices. The product is characterized by its affordability, user-friendly interface, and notable efficacy in mitigating both traditional and emerging security risks.
Cost:
- MAV Plus: $34.99/year
- MTP 10 Device Plan: $64.99/year
- MAV Plus 2 Yr.: $19.99/year
#8) AVG
Best for Small to mid-sized enterprises
Cost: Starts at $46.99/year per device
AVG provides a robust cybersecurity solution that is advantageous for small and medium-sized organizations. The gadget is equipped with a comprehensive range of advanced capabilities that are essential for safeguarding office devices against potential risks originating from both internal and external sources. The software possesses a high level of sophistication, enabling it to effectively safeguard computer systems against the most recent forms of viruses, ransomware, and malware threats that currently exist.
Features:
- Smart Scanner
- Identity Protection
- File Shredder
- File Server Security
- Remote Access
Category: Small business antivirus and firewall protection tool
Verdict: AVG offers a user-friendly cybersecurity solution that can be easily installed to provide continuous protection against both existing and emerging threats across all of your devices. The program is reasonably priced and equipped with a wide range of functions to ensure comprehensive protection against potential threats.
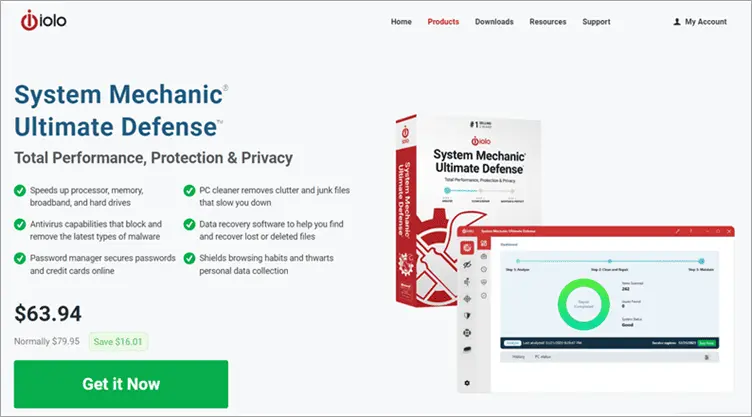
#9) System Mechanic Ultimate Defense
Best for AI and Algorithm Powered Threat Detection.
Cost: $63.94 annual plan.
System Mechanic Ultimate Defense functions as a proficient PC optimization tool and robust cybersecurity software. Real-time anti-virus protection may effectively safeguard personal computers against various dangers, including viruses, spyware, and other malicious entities. The system utilizes advanced threat detection algorithms and artificial intelligence (AI) to effectively identify novel and unfamiliar dangers prior to their potential infliction of harm on the system.
Features:
- Safeguards online passwords and payment card information from unauthorized access on the internet.
- Utilizes sophisticated artificial intelligence algorithms to identify and eliminate contemporary malware vulnerabilities.
- The objective is to identify and eliminate bloatware that hampers system performance.
- Utilize exclusive technological advancements to conduct analysis on files exhibiting questionable characteristics.
Category: On-Premise and Cloud-based Threat Detection.
Verdict: A comprehensive discussion on cybersecurity software would be insufficient without the inclusion of System Mechanic Ultimate Defense. The software possesses the capability to identify both novel and preexisting dangers by leveraging sophisticated artificial intelligence and algorithms. This particular cybersecurity software should be considered for attention if it has not already been acknowledged.
#10) Vipre
Ideal for providing full security against constantly developing threats.
Cost: Vipre business protection offers three pricing plans, namely Core Defense, Edge Defense, and Complete Defense, each priced at $96 per user per year for Core Defense and Edge Defense, and $144 per user per year for Complete Defense. The initial cost for home protection begins at $14.99 for the inaugural year.
Vipre provides cybersecurity solutions that cater to both personal and professional contexts. This software provides protection against several forms of cyber threats, including computer viruses, ransomware, and identity theft.
In order to safeguard corporate interests, it is capable of offering a full range of measures including email and end-point security and privacy, as well as real-time threat intelligence. This implementation offers a multi-tiered security mechanism for safeguarding your enterprise and its affiliated entities. The software is compatible with both Windows and Mac operating systems.
Features:
- Vipre offers streamlined solutions aimed at safeguarding businesses against internet attacks and potential data vulnerabilities.
- The company offers comprehensive packages and flexible price options that can be adjusted according to individual needs.
- The utilization of AI technology ensures an exceptional level of protection.
- Vipre provides a comprehensive and seamlessly integrated solution that is straightforward to implement and oversee.
- Additionally, it has the ability to offer email encryption functionalities.
Category: Cloud-based email and endpoint security solutions, as well as anti-virus software, are commonly utilized for personal use at home.
Verdict: Vipre is simple to implement and operate. It offers home protection, endpoint security, and email security options. It offers comprehensive cybersecurity protection by combining DLP and business VPN. Additionally, it can offer security awareness instruction.
Why Cyber Security Software Tools Are Important For Business?
In the current surroundings, defined by the potential for substantial financial ramifications and reputational damage resulting from data breaches, the indispensability of cyber security tools becomes evident. The primary functions of asset protection professionals include safeguarding a company’s resources, facilitating seamless operational processes, cultivating stakeholder confidence, and aiding in adherence to regulatory requirements. In light of the ever-evolving nature of cyber threats, the use of effective cybersecurity software is not merely discretionary, but rather a need for contemporary enterprises.
FAQs
About Cyber Security Software
1: Which software is used to monitor cyber crime?
The monitoring of cybercrime is predominantly conducted through the utilization of software within the realms of cybersecurity and digital forensics techniques. These tools facilitate the identification, mitigation, examination, and management of cyber threats and incidents. The following is a compilation of frequently employed software tools utilized in the monitoring and investigation of cybercrime:
- Intrusion Detection Systems (IDS) and Intrusion Prevention Systems (IPS):
- Snort,
- Suricata,
- Security Information and Event Management (SIEM) Systems:
- Splunk,
- LogRhythm,
- Digital Forensics Tools:
- Autopsy,
- EnCase Forensic,
- FTK (Forensic Toolkit),
- Network Monitoring and Analysis:
- Wireshark,
- Nmap,
- Threat Intelligence Platforms:
- MISP (Malware Information Sharing Platform & Threat Sharing),
- Endpoint Detection and Response (EDR) Tools:
- CrowdStrike Falcon,
- Sandboxing and Behavior Analysis Tools:
- Cuckoo Sandbox,
- FireEye,
- Honeypots and Deception Technology:
- Honeyd,
- VPN and Tor Detection:
- ExoneraTor,
- Dark Web Monitoring:
- Flashpoint,
2: Should I learn C or C++ for cyber security?
The selection between C and C++ for the field of cybersecurity is contingent upon various factors, including one’s objectives, existing proficiencies, and specific domains within cybersecurity that pique their interest. Presented below is a comparative analysis aimed at facilitating an educated decision-making process:
C Programming:
- Foundation,
- System Programming,
- Performance,
- Widely Used, etc.
C++ Programming:
- Object-Oriented,
- Versatility,
- STL (Standard Template Library),
- Modern Applications, etc.
3: Does cybersecurity use Python or C++?
Python and C++ possess unique roles and applications within the domain of cybersecurity. The following is an analysis of the utilization of each language:
Python in Cybersecurity:
- Scripting and Automation,
- Malware Analysis,
- Tool Development,
- Forensics,
- Web Security, etc.
C++ in Cybersecurity:
- Performance-Intensive Applications,
- Malware Development,
- Reverse Engineering,
- System-level Security,
- Game Hacking, etc.
4: Which Python is used in cyber security?
Python 3 is the current and actively maintained version of Python, and its adoption has been growing steadily in the cybersecurity community.
5: Where is cyber security mostly used?
The application of cybersecurity is pervasive throughout diverse sectors and industries, rendering it an essential element inside contemporary digital environments. The following are key domains in which cybersecurity is predominantly employed:
- Government and Defense,
- Banking and Finance,
- Healthcare,
- Retail and E-commerce,
- Energy and Utilities,
- Telecommunications,
- Education,
- Manufacturing,
- Transportation and Automotive,
- Smart Cities and Infrastructure,
- Individual Consumers,
- Cloud Services and Data Centers,
- Entertainment and Media, etc.
6: What is IT security tools?
IT security tools encompass a comprehensive array of software and hardware solutions that are specifically developed to safeguard, monitor, identify, and alleviate risks posed to information systems. These tools are designed to ensure the preservation of data and IT resources by protecting their integrity, confidentiality, and availability. The following is an analysis of frequently employed information technology security tools:
- Firewalls,
- Antivirus and Anti-malware Solutions,
- Intrusion Detection and Prevention Systems (IDPS),
- Virtual Private Network (VPN),
- Encryption Tools,
- Security Information and Event Management (SIEM),
- Multi-Factor Authentication (MFA) Tools,
- Web Application Firewalls (WAF),
- Network Scanners,
- Password Managers,
- Endpoint Detection and Response (EDR),
- Patch Management Tools,
- Digital Forensics Tools,
- Honeypots,
- Backup Software,
- Secure Configuration Management Tools, etc.
The Bottom Line
To wrap up, we would like to say that several cyber security software is there in the market that has been widely used by cyber security experts all over the world. In this regard, persons who have a keen interest in knowing more about this versatile cyber security software used by cyber security experts should contact Bytecode Security’s highly excelled training mentors with many years of quality experience. Here, at Bytecode Security, a dedicated learner can join highly lucrative cybersecurity courses that will certainly hone the skills of hacking enthusiasts to become full-fledged Cybersecurity Professionals in the near future.