
Web Application Security Course in Delhi
Bytecode’s Cyber Security – a subsidiary unit of Craw Cyber Security Institution is all set to deliver its most authentic Web Application Security Course in Delhi through a verified and fully accredited curriculum possessing all necessary qualifications to enhance the knowledge quotient of our understudies. During the sincere web application security course, one will grab all the required nitty-gritty details to capture the world-class accessible form of web application security course education to hold a good position in a genuine IT enterprise. In this course, all the students will get the needful web pentesting course fundamentals.
Web Application Security Course Content
Web Application Security Course in Delhi covers 26 comprehensive modules
- Module 01 : Improper Neutralization of Special Elements Used in an OS Command (‘OS Command Injection’)
- Module 02 : SQL Injection
- Module 03 : Code InjectionModule 03 : Code Injection
- Module 04 : Unrestricted Upload of File with Dangerous Type
- Module 05 : Inclusion of Functionality from Untrusted Control Sphere
- Module 06 : Missing Authentication for Critical Function
- Module 07 : Improper Restriction of Excessive Authentication Attempts
- Module 08 : Use of Hard-coded Credentials
- Module 09 : Reliance on Untrusted Inputs in a Security Decision
- Module 10 : Missing Authorization
- Module 11 : Incorrect Authorization
- Module 12 : Missing Encryption of Sensitive Data
- Module 13 : Cleartext Transmission of Sensitive Information
- Module 14 : XML External Entities
- Module 15 : External Control of File Name or Path
- Module 16 : Improper Authorization
- Module 17 : Execution with Unnecessary Privileges
- Module 18 : Use of Potentially Dangerous Function
- Module 19 : Incorrect Permission Assignment for Critical Resource
- Module 20 : Improper Neutralization of Input During Web Page Generation (‘Cross-Site Scripting’)
- Module 21 : Use of Externally-Controlled Format String
- Module 22 : Integer Overflow or Wraparound
- Module 23 : Use of a Broken or Risky Cryptographic Algorithm
- Module 24 : Use of a One-way Hash Without a Salt
- Module 25 : Insufficient Logging and Monitoring
- Module 26 : Download of Code Without Integrity Check
Top-Notch Web Application Security Training Course
We offer a very long-lasting study experience in web application security training course in the vicinity of Delhi NCR. You will get the web security course from the most skilled and experienced teaching faculties having more than 10 years of industry experience from the most reputed IT enterprises in India. Bytecode Security – the best web application security training institute in Delhi NCR will offer you world-class teaching trainers and state-of-the-art premises to study the most authentic and significant web pentesting course.
Training Course Duration
- Course Duration: 40 Hours
- Course Level: Intermediate
- Include: Training Certificate
- Language: English, Hindi
- Course Delivery: Classroom Training
- Course pdf: Click here to Download
You will learn in Web Application Security Training in Delhi
In this vast web application security course, a dedicated learner will get a deep understanding of various fundamental concepts associated with the web application penetration testing course which will help students to get a primetime job in information security domains. One will get briefed about numerous vulnerabilities like SQL Injection, XSS, PHP Injection, Indirect Object Reference, CSRF, and many more.
A learner will grab an authentic web application security certification that will be valid in almost all types of major and minor IT organizations and the same learner will definitely be able to apply for any web developer position whichsoever comes for the recruitment process. In addition, Bytecode Security has been remarked as the best application security training partner that authenticates students with the best-in-class training modules that will certainly help them to grasp all the fundamentals of web application security course protocols.
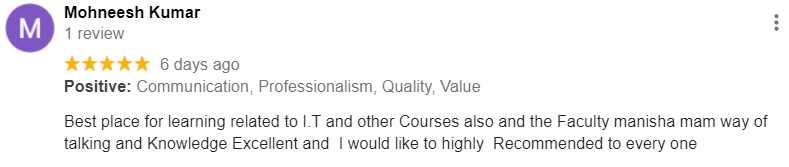
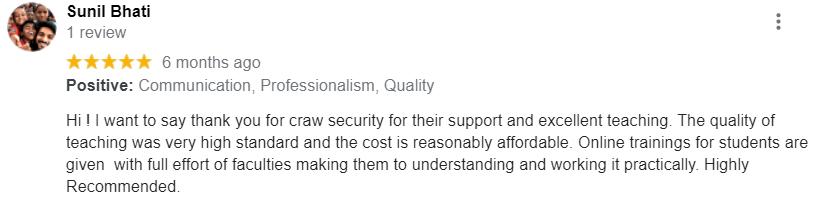
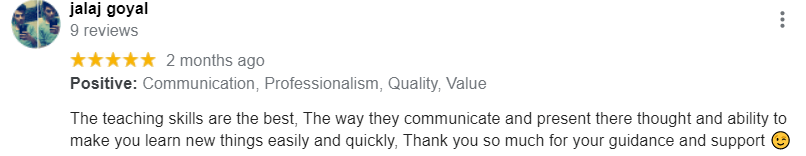
Web Application Security Course Review


Frequently Asked Questions
Web Application Security Course in Delhi | Web application security training and certification
The most crucial methodology to safeguard a web application security is as follows:
- Do proper testing and keep up with the security protocols while developing a web application.
- Encrypt your data.
- Use Exception Management.
After finding the concerned vulnerabilities, threats, and loopholes in a web application, a potential attacker initiates a series of coding attacks on the same web application which is strictly known as a web application attack.
SQL Query Injection, also known as SQLI, is basically a common attack vector that utilizes some malicious entities (usually SQL codes) for backend database manipulation to gain data that was not meant to be shown. This kind of database might comprise any number of items, banking credentials, individual client sensitive information, sensitive company information, user lists, etc.
Yes, as cyber security is a bundle of 12 small courses that possess some hectic amount of study that becomes a bit stressful sometimes. The numerous jobs related to cyber security pay very high amounts of salaries to various cyber security professionals, which is also a very authentic reason for many people to select this cyber security course.
Web Security is a term used to describe the security protocols and parameters utilized for safeguarding web applications by a sincere information security practitioner. This is a very integral part of cyber security where a number of cyber attacks are done on websites and web applications to steal their sensitive and crucial datasets.
The main prominent Web Security Requirements are as below:
- Authentication,
- Authorization,
- Data Protection, and
- Nonrepudiation.
There is nothing in this technological world that is fully secured but with a genuine web application security practitioner it is likely possible to safeguard the web apps. A person having a keen interest in learning the various protocols associated with web application security course can opt for this course at the magnificent facilities of Bytecode Security.
Web security is a process of securing information confidentiality concerning web applications by information security professionals. Generally, web application security comprises databases, software, applications, servers, and devices.
In general, any website gets hacked when a potential hacker finds hidden vulnerabilities in a web application’s security system and tries to manipulate the information using various methods. Any website hacks usually fall into these three categories such as:
- Access Control,
- Software vulnerabilities, and
- Third-party integrations/ services.
Course Overview
- Course Name : Basic Networking
- Course Level : Intermediate
- Language : Hindi English
- Course Delivery : Online / Classroom Training
- Include : Training and Certificate
- Course pdf : Click here to Download
6 Month Diploma Course
Related Cyber Security Courses
Information Security and Cyber Security Training and Certification Training Course provided by Bytecode Cyber Security in Delhi.
Free Demo Class
Web Application Security Course Review





Frequently Asked Questions
- Maintain Security During Web App Development.
- Encrypt your data.
- Use Exception Management.
The key Web services security requirements are authentication, authorization, data protection, and nonrepudiation. Authentication. Authentication ensures that each entity involved in using a Web service—the requestor, the provider, and the broker (if there is one)—is what it actually claims to be.
Web Security provides the protection and security to the website from the several criminals and threats.
There are 7 types of security threats:
- Malware
- Emotet
- Denial of service
- Man in the middle
- phishing
- SQL injection
- Password attack
The Website hacks almost three fall into categories: Access Control, Software vulnerabilities and last is third party integrations/services.
Call for support
+91 951 380 5401Follow us
R31/ 32, 2nd floor Vikas marg,
Shakarpur, New Delhi 110090
Jandu Tower
Training and Certification Course in Delhi
Recent Post
Recent Posts
-
Best Cybersecurity Winter Internship Training Course 2025 February 25, 2024
-
Importance of Social Media Security – You Must know February 19, 2024
-
Start Your Career in Cyber Security Courses After 12th February 12, 2024
Address
R31/ 32, 2nd floor Vikas marg,
Shakarpur, New Delhi 110090
Jandu Tower
Landline No: 011-4504 0849″
Mobile No: +91 951 380 5401
www.bytec0de.com
training@craw.in














