Best Cyber Security Course in Delhi with Job Assistance
Learn the genuine Diploma in Cyber Security Course through the versatile and highly talented information security experts hailing from multiple reputed IT enterprises all over the world. The diploma in cyber security is facilitated by state-of-the-art elevations of Bytecode Cyber Security Institution at Saket and Laxmi Nagar educational branches. In this course, a learner will grab authentic knowledge of 12 fundamental courses such as the Ethical Hacking Course, Penetration Testing Course, Python Programming Course, Cyber Forensics Investigation Course, and many others.
Training Available 24*7 Call at +91 9513805401
Learn Best Cyber Security Course in Delhi
1 Year Diploma In Cyber Security CourseThis authentic 1 Year Diploma in Cyber Security Course in Delhi NCR location is fully optimized by several information security experts through a genuinely verified curriculum by many professionals at various stages. One will grab all the necessary knowledge to become a superb and successful cyber security personnel in any reputed IT organization or a budding start-up in the near future after successfully completing this magnificent cyber security diploma course. A student will have the below-mentioned courses one by one to understand the fundamentals of cyber security nicely and effectively.
Cyber Security Meaning
Cybersecurity, often known as “cybersecurity,” is the collection of measures and practices aimed at safeguarding computer systems, networks, and digital resources from unauthorized access, attacks, harm, theft, or any other type of cyber peril. The field of information security comprises a diverse array of technologies, methodologies, and strategies that are specifically developed to protect information technology infrastructure, data, and services against potential threats and risks.
The domain of cybersecurity holds significant importance in the contemporary era of interconnected digital systems, wherein technology serves as a critical foundation for the operations of enterprises, individuals, and governments alike.
Expand Your Career Opportunities With
Introducing 1 Year Diploma in Cyber SecurityCyber Security Courses after 12th
This high-end 1 Year Diploma in Cyber Security Eligibility Criteria is a valid 12th certification from a recognized board anywhere in the world. A person can certainly go the cyber security course after 12th standard from a recognized board and make a promising career in this domain and get a high-paying salary job in the coming future. This beneficial Diploma in Cyber Security Course after 10th is curtailed in such a way that it offers the best possible training with required facilities which makes the students understand every aspect of learning effectively and efficiently.
Importance of Cyber Security in Career
The significance or importance of cybersecurity in an individual’s professional trajectory cannot be overemphasized. The demand for proficient cybersecurity workers is experiencing a significant spike as technology becomes more deeply integrated into various domains of business and everyday activities. A robust grounding in the field of cybersecurity not only grants individuals access to a diverse array of professional prospects but also guarantees the protection and authenticity of digital resources.
In addition, this course is notably essential for the protection of sensitive data, mitigation of cyber threats, and progression within the dynamic realm of technology-driven professions. Cybersecurity, in its essence, is not merely a talent but rather a career facilitator that plays a significant role in fostering personal and professional advancement within the context of the digital age.
Cyber Security Course with Placement Assistance
Introducing 1 Year Diploma in Cyber SecurityCyber Security Courses after 10th
Enroll in our comprehensive Cyber Security Course with Placement Assistance at Bytecode Security to commence a rewarding career in the field of cybersecurity. The curriculum has been specifically developed to provide individuals with the necessary information and abilities required to achieve success in the ever-evolving domain of cybersecurity. This Cyber Security Course for Beginners encompasses a diverse variety of subjects, including network security, ethical hacking, risk management, and compliance.
After the successful completion of the course, our diligent placement assistance team will make concerted efforts to establish connections between you and prominent firms seeking cybersecurity professionals. We cordially invite you to participate in Bytecode Security’s 1 Year Diploma Cyber Security Course in Delhi, where we aim to assist individuals in attaining a lucrative role within the cybersecurity sector.
Cyber Security Diploma Course in Delhi
It Includes 12 Cyber Security Diploma Courses and Get Job Assistance
Best Institute for Cyber Security Course
Introducing 1 Year Diploma in Cyber SecurityThe selection of an optimal institution for a Cyber Security Course is dependent upon individual requirements, geographical proximity, and professional aspirations. Nevertheless, numerous esteemed universities and organizations across the globe provide exceptional cybersecurity degrees and certificates.
In this context, Bytecode Security is also a name of Best Institute that provides leading cybersecurity education to all interested learners in the vicinity of Delhi NCR at Saket and Laxmi Nagar locations. All the course materials that you will get here are scrutinized by genuine credible cybersecurity experts.
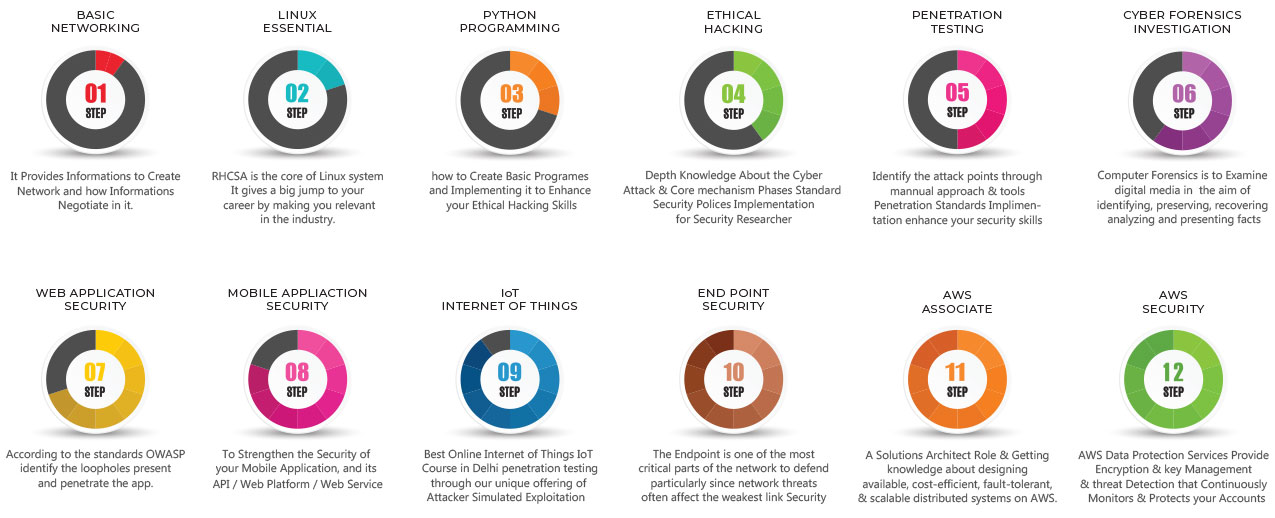
Get Cyber Security Course Syllabus
Basic Networking
Linux Essentials
Python Programming
Ethical Hacking
Advanced Penetration Testing
Cyber Forensics Investigation
Web Application Security
Mobile Application Security
IoT Penetration Testing
Endpoint Security
AWS Associate
AWS Security
Why Choose Bytecode for Cyber Security?
To learn more about cyber security with all the basic fundamentals, you can choose Bytecode Security for the best cyber security training in the region of Delhi NCR. Moreover, you may choose Bytecode Security for the following reasons:
Bytecode Security offers “Placement Assistance” services aimed at facilitating students’ access to employment prospects within the cybersecurity sector by establishing connections with prospective businesses.
To learn more about cyber security with all the basic fundamentals, you can choose Bytecode Security for the best cyber security training in the region of Delhi NCR. Moreover, you may choose Bytecode Security for the following reasons:

Cyber Security Course Eligibility: Cyber Security Course After 12th
Pursuing a cybersecurity course after the completion of 12th-grade education can be seen as a prudent and gratifying decision, given the escalating importance of cybersecurity in the contemporary digital landscape. Bytecode Security can do wonders for you in this domain by providing you with a world-class cyber security course after 12th. In this context, we also provide you with a genuine Cyber Security Course After 10th standard with the same 1 Year Diploma in Cyber Security Course under the prime guidance of highly qualified training mentors in the cyber security domain with all efficiency and credibility.
Frequently Asked Question
Student Review About Diploma Course | Cyber Security Course in Delhi
We rely too much on digital platforms. We share our daily routine-related content online every single day, along with the location of the content creation. This made it possible to target people’s social media platforms to snatch the data of those people via malware and malicious techniques.
With the help of that, they get benefitted monetarily. Now, you need to prepare a protective layer over your databases so that adversaries must not get to your databases. For that, you need the help of Cyber Security Skills.
Moreover, in this, only a Cyber Security Course is reliable for you. You can get this course under the premises of Bytecode Security with professional trainers. What are you waiting for? Enroll, Now!
Of course, Cyber Security is a great career path you can follow for a better career option. In this career path, you’ll be able to meet several professionals who are already so much trained in such skills and operating on so many devices related to various organizations.
Moreover, this career path can allow you to work for various reputed job profiles in the IT Sector. What are you waiting for? Choose your career options wisely!
For that, first, you can search for the best institute that can offer you a course related to cyber security. Afterward, they will teach you the fundamentals of cyber security from the begging.
Now, where can you get the best course for cyber security? Bytecode Security offers the Best Cyber Security Course in Delhi with 100% Job Placement. Under Bytecode Security, you’ll get support from the best-qualified trainers with years of experience in IT Security practicing on various cybersecurity cases. What are you waiting for? Contact, Now!
There is no exception when it comes to learning Cyber Security. Those who want to learn cybersecurity can search for available options to learn cybersecurity. However, having a special stream side could be better, as if you are from the Computer Science faculty, you’ll be able to perform faster than the rest of them.
Moreover, if you’re a beginner in the cyber security field, you need to chase an institute that offers training for cyber security. Bytecode Security can be the opportunity for you to learn cyber security.
They have been offering the Best Cyber Security Course in Delhi for a long time in the industry of Information & Technology! What are you waiting for? Contact, Now!
Well, there are no prerequisites for the Cyber Security Course if you enroll with Bytecode Security. However, if you have a Degree in Computer Science, IT, Systems Engineering, or a similar field, you can fastly grab the subject. You can be more productive than others in performing cybersecurity techniques. So, what are you waiting for? Enroll, Now!
1. Human Layer.
2. Perimeter Security Layer.
3. Network Layer.
4. Application Security Layer.
5. Endpoint Security Layer.
6. Data Security Layer.
7. Mission-Critical Assets.
Bytecode Security has been offering cybersecurity courses in the IT Sector for a long time and never have been backed up by any situation that arises for organizations related to cybersecurity/ cyberattacks.
As an institute, it provided quality education to the students with professional and experienced trainers under one roof from many states. For more, connect to our counselors.
+91 9513805401
Several institutes are trying to get more n more students to enroll on their premises. However, to provide a professional course for the upbringing of future cyber security experts, they would need professional trainers to guide them on how to testify their level of knowledge in cyber security with the latest techniques and tools valid in organizations for protecting their systems.
Bytecode Security offers the Best Cyber Security Course in Delhi with 100% Job Placement for cyber security aspirants for a long time in IT Sector. Moreover, you can get this course on a very pocket-friendly budget from Bytecode Security. Find out more by contacting Bytecode Security!
To work as a professional cybersecurity expert, you need the following skills to prove your honed skillsets.
- Network and System Administration
- Knowledge of Operating Systems and Virtual Machines
- Network Security Control
- Coding
- Cloud Security
- Blockchain Security
- The Internet of Things (IoT)
Artificial Intelligence (AI)
Definitely, anyone can learn cybersecurity skills if they want to. There are several sources via which you can learn such skills in which you will learn how to perform penetration testing over machines with the latest techniques and tools.
Ex – Books, Ebooks, Online Videos, and Courses. The best option, as a beginner, you can choose is to join a Course. For you, Bytecode Security offers the Best Cyber Security Course in Delhi with 100% job placement.
After Joining this course, you’ll be able to understand the concepts of cyber security with the support of professional trainers to guide you through n through. Moreover, you can get a certification from Bytecode Security after completing this course.
This certificate will work for you as professional evidence of your honed skills in cyber security in most MNCs. For more information, contact Bytecode Security!
The process of preventing unwanted access to or attacks on computer networks and systems is known as cybersecurity. To keep their assets and data safe from hackers, individuals, companies, and governments all need to make cybersecurity investments.
The prominent cyber forensics tools are mentioned as follows:
Network Forensic tools.
Database analysis tools.
File analysis tools.
Registry analysis tools.
Email analysis tools.
OS analysis tools.
Disk and data capture.
Linux Essentials is a course widely referred to as Linux Essentials Course offered by many Linux and Red Hat Inc. affiliated institutions such as Bytecode Security – a subsidiary unit of Craw Cyber Security Institute. In this course, one will learn about the introduction of Linux as an operating system, basic open-source concepts, and the fundamentals of the Linux command line.













